If you want to add a router to a network in gns3 you should have a router image added to it.
By default gns3 wouldnt have any router images in it. One should manually download and add the images to gns3.
In this tutorial I will show you how to add router image to GNS3
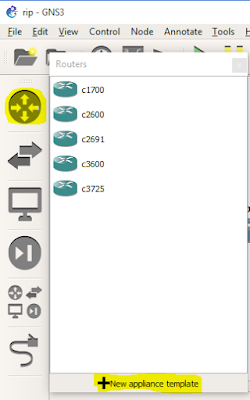
Click on the button for browsing routers (highlighted in the screenshot)-->Then click on New appliance template
By default gns3 wouldnt have any router images in it. One should manually download and add the images to gns3.
In this tutorial I will show you how to add router image to GNS3
Click on the button for browsing routers (highlighted in the screenshot)-->Then click on New appliance template
Then select new image button
Use browse option to select the path where ios image exists
Once the ios image is selected you will get a popup asking whether to decompress it or not .Select 'Yes'
Then click on next it will ask you for the name and platform for this ios image
Then you can click on next until it is finished. There will be so many options for which you can configure it, but it is much better to keep them as like it
Once it is configured you will get a screen the new ios image is shown along with other installed router templates as shown below.
Then you can use the configured router from the router option